- Messages
- 414
- Reaction score
- 636
- Points
- 268
https://www.cnet.com/culture/featur...rs-are-paving-the-road-to-nuclear-armageddon/
North Korea's Crypto Hackers Are Paving the Road to Nuclear Armageddon
North Korea has quietly become a cryptocurrency superpower. It has stolen billions in bitcoin and ether and is funneling profits to its nuclear weapons program.
It was an astonishing interview for recruiter Elliott Garlock. While screening candidate engineers for a crypto firm in February, Garlock encountered one applicant who raised almost every conceivable red flag.
The interviewee joined the Zoom interview with his camera off and had to be cajoled into turning it on. There was constant chatter in the background, like he was jammed in a small, crowded room. He claimed to be from San Francisco but, when pressed, wasn't able to pinpoint his location more precisely than "Bay Area."
It was a strange and unproductive interview. Worst of all, it was the first of many. Garlock, the founder of the Stella Talent Partners recruitment firm, soon encountered another, nearly identical candidate. Then another, and another and another.
"I got annoyed after a while, because it was a total waste of time," Garlock said. "I originally thought the scam was that they were offshore, trying to take advantage of remote work to just get a salary for not working."
Now there's a new hypothesis: The people interviewing for jobs were North Koreans trying to siphon money to the reclusive nation. That's in accord with warnings from both the FBI and the Treasury Department, which have cautioned about North Korea's escalating risk to the cryptocurrency industry.
The danger is more than theoretical, as one catastrophic hack in March showed. The Lazarus Group, a hacking outfit associated with North Korea's government, managed to drain over $600 million in crypto from a blockchain used by NFT game Axie Infinity. North Korean hackers stole $840 million in the first five months of 2022, according to Chainalysis data, over $200 million more than they'd plundered in 2020 and 2021 combined.
That is of extraordinary consequence. About a third of the crypto North Korea loots goes into its weapons program, including nuclear weapons, estimates Anne Neuberger, a deputy national security adviser in the Biden administration. It's also funneled to the country's espionage operations. When two South Koreans earlier this year were revealed to have been stealing military information for a North Korean spy, it turned out they'd been paid in bitcoin.
"Crypto is arguably now essential to North Korea," said Nick Carlsen, a former North Korea analyst at the FBI who now works for crypto security firm TRM Labs. "By any standard, they are a crypto superpower."
A crypto superpower with nuclear weapons, that is. A country whose crypto prowess, North Korea watchers say, is directly funding the development of those nukes, with the odds of a new nuclear weapons test growing. The rogue nation has been ratcheting up ballistic missile tests in the past 10 days: Over 5 million residents of Japan were told to seek immediate shelter on Wednesday after North Korea launched a missile over the island of Hokkaido. It's highly likely this, too, was funded at least in part by stolen cryptocurrency.
The Democratic People's Republic of Korea, as North Korea is formally known, has come to depend more on crypto since the pandemic began. It historically relied on black market trade, exporting coal, meth, cigarettes and labor to Southeast Asia, Russia and especially China. But the zero COVID strategy of leader Kim Jong Un has closed borders, thinning the country's already slight revenues. Trade with China, by far North Korea's biggest economic partner, fell 80% in 2020, and reports of food shortages abound. At the same time, cryptocurrency values have skyrocketed.
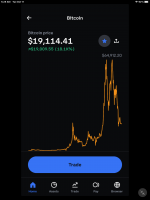
Despite the recent crypto crash, bitcoin is trading 250% higher than before the pandemic. Ether, the second biggest cryptocurrency, is up over 700%.
Garlock estimates he encountered a dozen candidates he now considers North Korean operatives between February and April. None of them got referred to one of his client companies, which is lucky. North Korean hackers have shown they can cause immense damage if they manage to dupe just one person.
Axie Infinity is a web browser game similar to Pokemon, except that the Axie creatures you battle are owned as NFTs and can be traded for crypto. To support this digital economy, developer Sky Mavis created its own blockchain called Ronin, whose sole purpose is to process Axie Infinity transactions. At its peak in August 2021, the game was generating over $15 million a day. A senior engineer who worked on Ronin was approached by North Korean operatives on LinkedIn earlier this year, according to a report from The Block. After several rounds of interviews, the engineer received a formal job offer via PDF.
The Ronin blockchain runs on a proof-of-authority model, wherein validation control is given to nine handpicked accounts. To gain control of the blockchain, bad actors needed to control five of these nine validator accounts. When the senior engineer clicked the infected link, he unwittingly gave North Korean hackers keys to four of those validators. Once they were inside Axie Infinity's computer system, hackers were able to get keys for a fifth. The $600 million was drained shortly after.
Sky Mavis didn't respond to a request for comment. But in a post-mortem published in April, the company said: "Sky Mavis employees are under constant advanced spear-phishing attacks on various social channels and one employee was compromised. … The attacker managed to leverage that access to penetrate Sky Mavis IT infrastructure and gain access to the validator nodes."
It's possible the North Korean operatives hired a middleman company to orchestrate the faux employer phishing scheme. That's what they did in 2019, paying an actor to play an executive in fake job interviews with the goal of infiltrating the computer systems of Chile's Redbanc. (North Korea never got to steal from the bank, thanks to an eagle-eyed IT guy, who saw suspicious activity on the network.)
It's tempting to write off the Ronin hack as a disorganized crypto company being exploited. But the same tactics have worked against world-renowned targets. The infamous Sony hack of 2014, a response to the studio's distribution of Seth Rogan's The Interview, a comedy about an assassination attempt on Kim, was achieved in much the same way. Hackers gained access to Sony's computer network by pretending to be a businessman, former assistant US attorney Tony Lewis told the BBC.
North Korea's Crypto Hackers Are Paving the Road to Nuclear Armageddon
North Korea has quietly become a cryptocurrency superpower. It has stolen billions in bitcoin and ether and is funneling profits to its nuclear weapons program.
It was an astonishing interview for recruiter Elliott Garlock. While screening candidate engineers for a crypto firm in February, Garlock encountered one applicant who raised almost every conceivable red flag.
The interviewee joined the Zoom interview with his camera off and had to be cajoled into turning it on. There was constant chatter in the background, like he was jammed in a small, crowded room. He claimed to be from San Francisco but, when pressed, wasn't able to pinpoint his location more precisely than "Bay Area."
It was a strange and unproductive interview. Worst of all, it was the first of many. Garlock, the founder of the Stella Talent Partners recruitment firm, soon encountered another, nearly identical candidate. Then another, and another and another.
"I got annoyed after a while, because it was a total waste of time," Garlock said. "I originally thought the scam was that they were offshore, trying to take advantage of remote work to just get a salary for not working."
Now there's a new hypothesis: The people interviewing for jobs were North Koreans trying to siphon money to the reclusive nation. That's in accord with warnings from both the FBI and the Treasury Department, which have cautioned about North Korea's escalating risk to the cryptocurrency industry.
The danger is more than theoretical, as one catastrophic hack in March showed. The Lazarus Group, a hacking outfit associated with North Korea's government, managed to drain over $600 million in crypto from a blockchain used by NFT game Axie Infinity. North Korean hackers stole $840 million in the first five months of 2022, according to Chainalysis data, over $200 million more than they'd plundered in 2020 and 2021 combined.
That is of extraordinary consequence. About a third of the crypto North Korea loots goes into its weapons program, including nuclear weapons, estimates Anne Neuberger, a deputy national security adviser in the Biden administration. It's also funneled to the country's espionage operations. When two South Koreans earlier this year were revealed to have been stealing military information for a North Korean spy, it turned out they'd been paid in bitcoin.
"Crypto is arguably now essential to North Korea," said Nick Carlsen, a former North Korea analyst at the FBI who now works for crypto security firm TRM Labs. "By any standard, they are a crypto superpower."
A crypto superpower with nuclear weapons, that is. A country whose crypto prowess, North Korea watchers say, is directly funding the development of those nukes, with the odds of a new nuclear weapons test growing. The rogue nation has been ratcheting up ballistic missile tests in the past 10 days: Over 5 million residents of Japan were told to seek immediate shelter on Wednesday after North Korea launched a missile over the island of Hokkaido. It's highly likely this, too, was funded at least in part by stolen cryptocurrency.
The Democratic People's Republic of Korea, as North Korea is formally known, has come to depend more on crypto since the pandemic began. It historically relied on black market trade, exporting coal, meth, cigarettes and labor to Southeast Asia, Russia and especially China. But the zero COVID strategy of leader Kim Jong Un has closed borders, thinning the country's already slight revenues. Trade with China, by far North Korea's biggest economic partner, fell 80% in 2020, and reports of food shortages abound. At the same time, cryptocurrency values have skyrocketed.
Despite the recent crypto crash, bitcoin is trading 250% higher than before the pandemic. Ether, the second biggest cryptocurrency, is up over 700%.
Garlock estimates he encountered a dozen candidates he now considers North Korean operatives between February and April. None of them got referred to one of his client companies, which is lucky. North Korean hackers have shown they can cause immense damage if they manage to dupe just one person.
One bad click
A single corrupted file can leave disaster in its wake. The Axie Infinity hack that netted North Korea over $600 million in crypto started with just that: a tainted PDF.Axie Infinity is a web browser game similar to Pokemon, except that the Axie creatures you battle are owned as NFTs and can be traded for crypto. To support this digital economy, developer Sky Mavis created its own blockchain called Ronin, whose sole purpose is to process Axie Infinity transactions. At its peak in August 2021, the game was generating over $15 million a day. A senior engineer who worked on Ronin was approached by North Korean operatives on LinkedIn earlier this year, according to a report from The Block. After several rounds of interviews, the engineer received a formal job offer via PDF.
The Ronin blockchain runs on a proof-of-authority model, wherein validation control is given to nine handpicked accounts. To gain control of the blockchain, bad actors needed to control five of these nine validator accounts. When the senior engineer clicked the infected link, he unwittingly gave North Korean hackers keys to four of those validators. Once they were inside Axie Infinity's computer system, hackers were able to get keys for a fifth. The $600 million was drained shortly after.
Sky Mavis didn't respond to a request for comment. But in a post-mortem published in April, the company said: "Sky Mavis employees are under constant advanced spear-phishing attacks on various social channels and one employee was compromised. … The attacker managed to leverage that access to penetrate Sky Mavis IT infrastructure and gain access to the validator nodes."
It's possible the North Korean operatives hired a middleman company to orchestrate the faux employer phishing scheme. That's what they did in 2019, paying an actor to play an executive in fake job interviews with the goal of infiltrating the computer systems of Chile's Redbanc. (North Korea never got to steal from the bank, thanks to an eagle-eyed IT guy, who saw suspicious activity on the network.)
It's tempting to write off the Ronin hack as a disorganized crypto company being exploited. But the same tactics have worked against world-renowned targets. The infamous Sony hack of 2014, a response to the studio's distribution of Seth Rogan's The Interview, a comedy about an assassination attempt on Kim, was achieved in much the same way. Hackers gained access to Sony's computer network by pretending to be a businessman, former assistant US attorney Tony Lewis told the BBC.